New
May 11, 2010 8:07 PM
#1
| News regarding IT Security will be posted here. There will be at least a monthly posting regarding some computer security news. If there are special "out-of-band" notifications, they will be posted here immediately as well. Please refrain from posting your comments/discussion here. If you want to comment/discuss, please post it here. |
May 16, 2010 4:27 PM
#2
| ICPP Copyright Foundation is Fake There's a new extortion trojan in circulation. This one attempts to steal victims' money by bullying them to pay a "pre-trial settlement" to cover a "Copyright holder fine". The victim is informed that an "Antipiracy foundation scanner" has found illegal torrents from the system. If he won't pay $400 (via a credit card transaction), he might face jail time and huge fines.  And the warnings will not go away. They will reappear every time the user reboots his system.  All of this is completely fake. There is no "ICPP Foundation", and the messages will appear even if the system contains no illegal material whatsoever. Most importantly: Refuse to pay money to these clowns! If people pay them, the problem will only grow bigger. The group behind this have even set up an official-looking website at icpp-online.com.  The domain is registered to Mr. "Shoen Overns". The same e-mail address ovenersbox@yahoo.com has been seen before in various other domains, connected to Zeus and Koobface scams.  If you click on the Reports shown by the application, you'll end up on pages such as these:  We tried calling the (Italian) phone number listed on the page: +39 (06) 9028 0658. Unsurprisingly, it goes nowhere.  These pages are hosted at 91.209.238.2, which according to WHOIS belongs to EBUNKER-NET, a "High protected Somalia network". It's running in Moldova. This is what the payment page looks like:  There is no obvious credit-card payment system connected to the site; they just seem to collect the credit card information. If you are hit by this trojan, DO NOT PAY. Instead, use an antivirus program that is capable of detecting it to remove the trojan. F-Secure Antivirus detects it as Rogue:W32/DotTorrent.A. You can use our free Online Scanner at ols.f-secure.com to check your system. The malware is typically located in c:\documents and settings\USERNAME\application data\IQManager\iqmanager.exe. We've seen two versions so far. MD5 hashes of them are cedc2c35bf967027d609df13e937946c and bca3226cc1cfea416c0bcf488082e5fd. Source: F-Secure Weblog |
May 18, 2010 10:19 PM
#3
| Facebook Users Hit by Candid Camera Prank Attack In the latest wave of malware targeted to users of Facebook, there is now a "sexiest video" on the loose that actually installs the Hotbar adware on the user's computer if they click on the link. There will first be a message stating that the video player is out of date and ask the user to download a file. Following that, the same video would be posted to their contacts in Facebook.  The messages read: <name>, this is without doubt the sexiest video ever! :P :P :P accompanied by what appears to be a video with the title "Candid Camera Prank [HQ]". The message has what appears to be a movie thumbnail of a woman on a bicycle wearing a short skirt, and the video's length is given as 3:17. With the recent surge of malware hoaxes and links on Facebook, do exercise caution and don't click links if you think they're malicious. Source: Sophos Weblog |
May 19, 2010 6:35 PM
#4
| Embarrassing privacy flaw found on Facebook The flaw was discovered last week and reported to Facebook by M.J. Keith, a senior security analyst with security firm Alert Logic. The bug has to do with the way that Facebook checked to make sure that browsers connecting with the site were the ones they claimed to be. Facebook's servers use code called a "post_form_id" token to check that the browser trying to do something -- liking a group, for example -- was actually the browser that had logged into the account. Facebook's servers check this token before making any changes to the user's page, but Keith discovered that when he simply deleted the token from messages, he could change many settings on any Facebook account. "It's like putting locks on a bunch of stuff but not locking them," he said in an interview. Keith could make users' private information public, change or read profile information, even add new contact e-mail addresses, he said. "It's pretty bad; you can do a lot of damage with it," he said. Facebook worked with Alert Logic to fix the bug, known as a cross-site request forgery (CSRF), Facebook spokesman Simon Axten confirmed in an e-mail message. "It's now fixed," he said. "We're not aware of any cases in which it was used maliciously." But as of late Tuesday afternoon, Pacific time, after Axten sent his e-mail, Facebook had not completely fixed the issue. For testing purposes, Keith created a Web page with an invisible iFrame HTML element that he programmed in Javascript. When the IDG News Service clicked on this page while logged into Facebook, it made the Facebook user automatically "like" several pages with no further interaction. That's pretty much how an attack would have worked, Keith said. A victim would need to be tricked into clicking on a malicious Web site that contained the Javascript code that exploited the CSRF flaw. Facebook has been under a lot of heat recently by users who feel it hasn't done enough to protect their privacy, and embarrassing technical glitches like this don't help the social-networking company's case. Earlier this month, Facebook had to temporarily pull its chat feature, after another bug let users eavesdrop on their friends' private chat sessions. Source: PC World |
May 19, 2010 6:41 PM
#5
| New malware attack: watch_video.zip Email messages are being spammed out with a variety of lurid x-rated subject lines. Attached to the emails is a file called watch_video.zip, which contains malware that (at the time of writing) is not being detected by most anti-virus products. Emails with other subject lines can have different message bodies, albeit all of a similar pornographic nature. All of the messages (regardless of different subject lines and message bodies) contain the phrase: Open attached file to watch video Source: Sophos Weblog |
May 21, 2010 5:14 AM
#6
| Twitter Attack There's another malware run underway on Twitter. A fairly large pool of fake accounts are sending out messages with popular hashtags and the text "haha this is the funniest video ive ever seen".  People see these messages when they look for trending topics in Twitter. The shortlinks in the Tweets point to a page under pc-tv.tv, which uses a Java exploit to drop a keylogger / banking trojan combo to your system. The attack is unusually easy to follow by just looking at the source code of the page. (However, I disagree. This would require people to have basic knowledge of HTML, and of course be very current with malicious software on the loose.)  Source: F-Secure Weblog |
May 21, 2010 7:26 PM
#7
| Try not to laugh xD: Worm spreads via Facebook status messages A clickjacking worm spread quickly across Facebook earlier today, tricking users into posting it to their status updates.  The worm, which some have dubbed Fbhole because of the domain it points to, posts a message like the following: try not to laugh xD http://www.fbhole.com/omg/allow.php?s=a&r=<random number> (Please do NOT click the link!) Clicking on the link would display a fake error message that would trick you - through a clickjacking exploit - to invisibly push a button that would publish the same message to your own Facebook status update. We've seen clickjacking exploited by hackers before in attacks on social networks, for instance in the "Don't click" attack seen on Twitter in early 2009. The good news is that's effectively it. Rather like the "Don't click" Twitter attack, it appears that this latest Facebook security scare was more motivated out of mischief than money. Source: Sophos Weblog |
May 22, 2010 11:59 PM
#8
| Distracting Beach Babes video attack hits Facebook users Thousands of Facebook users are reporting that they have been hit by a malware attack posing as a video of young bikini-clad women on a beach. The messages are posted on the walls of Facebook members, seemingly from their friends and associates on the site, with a thumbnail which appears to be an image of a young woman's bottom in a bikini. The messages read: <name>, this is hilarious! lol :P :P :P Distracting Beach Babes [HQ] Length: 5:32 The "Distracting Beach Babes" scam appears to be the latest incarnation of the widespread "Sexiest Video Ever" assault we saw spreading on Facebook last weekend, installing adware onto victims' computers which can make money for the hackers behind the attack. And you shouldn't be in any doubt as to how successful a scheme like this can be. Many Facebook users are all-too-comfortable with receiving salacious videos and humourous links from their friends, and will click on them without a moment's thought. Unfortunately that can then begin a bombardment of malicious posts to their social networking contacts - do you really want a blitz like this unleashed in your name? Fortunately, some Facebook users are using the medium to warn each other of the threat:  If you have been hit, you should delete the offending message from your page, scan your computer with an up-to-date anti-virus, change your passwords, review your Facebook application settings. Also, learn an important lesson: don't be so quick to click on unsolicited links and approve unknown applications in the future. Perhaps most importantly, tell your friends to also do the same. Source: Graham Cluley, Sophos Weblog |
May 25, 2010 10:41 PM
#9
| Rogue Testimonials from Rogue Antivirus The same breed of character that brought you rogue customer service are adding to their con-artist repertoire with rogue product testimonials for their FakeAV. These obviously bogus “True life stories” are just another detail in the social engineering effort to convince victims of their product’s legitimacy.  The actual descriptions are oddly perverse. For example: Steve J. of New York had his software project stolen through a troyan that got into his computer through some internet site. Steve is still suffering from a strong depression… and Thomas S. lost his family over his passion for teen sex sites. His wife turned the computer on and some Teen Sex ad popped up. Next day she left and took both of their kids with her… Now I’m definitely thinking “I’ve gotta have this software. ” So what happens when you click the “Free Download” button ? You actually get redirected to a fraudulent payment processing site where you can purchase the software rather than download it. What’s more — the payment site is fully equipped with a genuine SSL certificate from a legitimate certificate authority.  The site uses a domain-validated SSL certificate, which can often be issued with little more than an email address, so they provide absolutely no assurance that the service behind the domain is legitimate. But in order to see the certificate is only domain-validated, you have to manually examine the certificate details and look at the full Subject field contents. Purchasing digital certificates from legitimate CAs is another angle on malware hiding in plain sight. We will all have to stay on our toes as the fraudsters continue to invest more time and real money into their malicious campaigns. Source: Sophos Weblog P.S: If you guys don't understand any terms here, please feel free to voice them out in the discussion topic. Cheers~ |
May 28, 2010 11:26 PM
#10
| Naughty Camera Prank virus hits Facebook users Reports are coming in that a new attack is spreading virally across Facebook, for the third Saturday in a row. The attacks come in the form of a message, sent by a rogue Facebook application, saying: <name>, this is without a doubt the most hilarious video ever. LOL! Naughty Camera Prank! [HQ] Facebook users are urged not to click on the videos. The attack follows one week after the "Distracting Beach Babes" video attack, which itself came seven days after Facebook was hit by another attack dubbed the "Sexiest Video Ever". In those examples, users who clicked on the video thumbnails were instead taken to an application that told them that if they wished to view the video they had to install an updated player onto their PC. The software downloaded by the users was, in reality, revenue-generating adware. Furthermore, when users gave permission to the Facebook application to execute, it spread the message virally to all of their Facebook friends. Hopefully, before too much harm is done, Facebook's security team will be hard at work shutting down the rogue applications sending these messages as soon as they pop up. If you made the mistake of clicking on the video link please play safe by: warning your friends who you may have passed the message onto, scanning your computer with an up-to-date anti-virus, changing your Facebook password, checking your application settings and removing any apps you don't recognise. Source: Graham Cluley, Sophos Weblog |
May 31, 2010 6:40 PM
#11
| Viral clickjacking 'Like' worm hits Facebook users Hundreds of thousands of Facebook users have fallen for a social-engineering trick which allowed a clickjacking worm to spread quickly over Facebook this holiday weekend. Affected profiles can be identified by seeing that the Facebook user has apparently "liked" a link:  Messages seen being used by the spammers include: "LOL This girl gets OWNED after a POLICE OFFICER reads her STATUS MESSAGE." "This man takes a picture of himself EVERYDAY for 8 YEARS!!" "The Prom Dress That Got This Girl Suspended From School." "This Girl Has An Interesting Way Of Eating A Banana, Check It Out!" Clicking on the links takes Facebook users to what appears to be a blank page with just the message "Click here to continue".  However, clicking at any point of the page publishes the same message (via an invisible iFrame) to their own Facebook page, in a similar fashion to the "Fbhole" worm we saw earlier this month. The trick, which uses a clickjacking exploit, means that visiting users are tricked into "liking" a page without necessarily realising they are recommending it to all of their Facebook friends. Unfortunately, as we're all too aware, messages such as "LOL This girl gets OWNED after a POLICE OFFICER reads her STATUS MESSAGE.", "This man takes a picture of himself EVERYDAY for 8 YEARS!!", "The Prom Dress That Got This Girl Suspended From School." and "This Girl Has An Interesting Way Of Eating A Banana, Check It Out!" are exactly the kind of content that people will click on on Facebook. Sophos detects the offending webpages as being infected by Troj/Iframe-ET. If you believe you may have been hit by this attack, view the recent activity on your news feed and delete entries related to the above links. Furthermore, you should view your profile, click on your Info tab and remove any of the pages from your "Likes and interests" section. Source: Graham Cluley, Sophos Weblog |
Jun 5, 2010 4:37 PM
#12
 Adobe's products are once again in the firing line, as hackers are reportedly exploiting critical unpatched vulnerabilities in the products Adobe Reader, Acrobat and Flash Player. Adobe has published a security advisory describing the problems which affect users regardless of whether they're running Windows, Mac OS X, Linux, Solaris or UNIX. Adobe has labelled the zero-day vulnerabilities as "critical", the most serious rating it has. Adobe says that Adobe Reader and Acrobat version 8.x are not vulnerable, and that the Flash Player 10.1 release candidate "does not appear to be vulnerable". Although Adobe has published a way to mitigate the problem for Adobe Reader and Acrobat 9.x for Windows, the workaround is clearly not ideal: Deleting, renaming, or removing access to the authplay.dll file that ships with Adobe Reader and Acrobat 9.x mitigates the threat for those products, but users will experience a non-exploitable crash or error message when opening a PDF file that contains SWF content. Mind you, maybe I wouldn't be so bothered about that in actual fact. After all, when would I ever want to open a PDF containing ShockWave Flash content inside it? Once again, it sounds as if feature-itis (the technical term for a product suffering from excessive inflation of unnecessary features) could have partly been Adobe's undoing in this example. A simple PDF reader without so many bells and whistles might not have suffered from such exploitation. Brad Arkin, director of product security at Adobe, says that the firm is working on a patch - although it is not yet known when it will be available. Source: Graham Cluley, Sophos Weblog |
Jun 6, 2010 7:21 PM
#13
Malware found lurking in apps for Windows Mobile Scammers are distributing apps for Windows Mobile-based smartphones that have malware hidden inside that makes calls to premium-rate numbers across the globe, racking up expensive bills unbeknownst to the phone's owner, a mobile security firm said on Friday. The apps--3D Anti-Terrorist game, PDA Poker Art, and Codec pack for Windows Mobile 1.0--are being distributed on as many as nine popular download Web sites, including DoDownload, GearDownload, and Software112, according to John Hering, chief executive and founder of mobile security provider Lookout. Someone has copied the programs and repackaged them with the malware inside, he said. Once the app is installed the virus wakes up and starts dialing premium-rate numbers like in Somalia and the South Pole, Hering said. He added that victims may not know about the problem until they get their phone bill and see that it's $50 or $100 higher than it should be. Auto-dialer scams are common in Russia and other countries but are still relatively rare in the United States. But that will change. Six months ago, Lookout saw four pieces of malware per 100 phones. Now, that figure has more than doubled to nine pieces of malware for every 100 phones, Hering said. Hering said Microsoft had been contacted about the issue, but that the problem is not due to any vulnerability in the Windows Mobile software and therefore can't simply be patched. "Users need to be aware of what they are downloading and make sure it is a reputable source and from a reputable developer," he said. Lookout is one of a growing number of companies that offer software and services to help protect mobile devices from malware and other threats. Microsoft is aware of the issue and is currently investigating it, said Jerry Bryant, group manager for Response Communications at Microsoft. "As always, Microsoft continues to encourage customers to follow all of the steps of the 'Protect Your Computer' guidance of enabling a firewall, applying all software updates and installing antivirus and antispyware software," he said. "While Microsoft does not have a mobile AV product we do detect and protect in certain scenarios. The general protect guidance also applies to mobile phone users: http://www.microsoft.com/protect/."; The hidden auto-dialing malware incidents are noteworthy because they signal a shift from attackers seeking mere notoriety to profit-motivated fraud, Hering said. "What took 15 years for malware to evolve on the desktop is accelerated on the mobile platform," he said. "We're seeing it move from early proof-of-concept (malware) to things that are driving profit." Source: Cnet News |
Jun 7, 2010 9:01 AM
#14
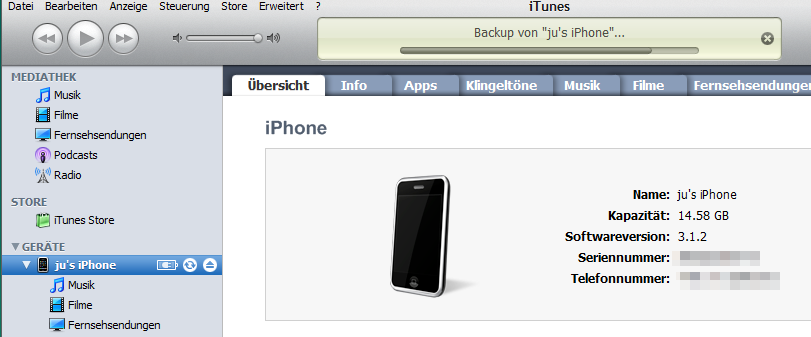 The iPhone's data leak is even more extensive than initially assumed. In initial tests, encrypted and locked devices essentially only disclosed music and images. However, The H's associates at heise Security have now managed to connect an iPhone with iTunes under Windows and created a full backup, including such sensitive data as passwords in clear text. The problem was initially discovered by Bernd Marienfeldt on an Ubuntu system. In that case the Ubuntu system displayed the various folders of a freshly booted iPhone although the phone was locked and had never had any contact with this Linux system before. A locked iPhone is supposed to refuse any communication with devices it doesn't know. However, if the iPhone is accessed while booting, this can frequently result in the phone pairing with unknown devices regardless of those protections. It appears that some system component hasn't finished booting when the connection request is made and, as a consequence, the iPhone's "lockdownd" daemon allows device pairing: 17:21:46 lockdown.c:818 lockdownd_do_pair(): ValidatePair success The problem, though, is not with Linux or Windows, but with the iPhone. Using the same technique, heise Security also managed to pair a Windows Vista system with an iPhone. While with Linux only a few selected folders on the iPhone were displayed, Windows allowed full system access. For instance, it was no problem to create a complete backup using iTunes, including items such as notes, text messages and even plain text passwords. Pairing wasn't possible with all devices. What exactly it is that determines whether the iPhone accepts a connection request remains unclear. It certainly isn't determined by the device type, because heise Security managed to trick 3G systems as well as 3GS systems. At least in one case, unwanted pairing became impossible after the iPhone's information about already paired devices was deleted. Apple has not yet answered heise Security's questions about whether and when this problem will be solved. Hector Martin and a couple of developers of the Linux packages have done some further research on this issue. Martin has come to the conclusion that the problem only occurs if the iPhone was shut down from an unlocked state. During the wake up this state is restored and the device is "open" for a short period of time before the Springboard application wakes up and locks it down. This short period is sufficient for a pairing to occur that ensures permanent access. An iPhone that was shut down in a locked state does not accept the pairing – which corresponds to heise Security's observations. This reduces the risk somewhat, because a lost iPhone in a locked state cannot be tricked into pairing. Source: ESET NOD32 Threatblog |
Jun 7, 2010 6:17 PM
#15
Spammers beat Steve Jobs in announcing new iPhone In a few hours time, at Apple's annual World Wide Developers Conference (WWDC) in San Francisco, Steve Jobs is widely anticipated to announce a new version of his company's iPhone to an expectant crowd. The feverish predictions of past occasions may be a little subdued this time, as a prototype device fell into the hands of Gizmodo back in April. In fact, one of the few hotly discussed questions remaining is what will the new iPhone be called? The iPhone 4G? Well, although that would make numeric sense after the 3GS model, as it is unlikely to support the 4G cellular network it seems unlikely. Regardless of its moniker, some spammers seem dead set on stealing Steve Jobs's thunder. At least judging by this spam campaign:  Wow! A free iPhone 4G! That's awfully kind of Apple. Hopefully no one would be silly enough to believe this email, even if it had been spell-checked properly. But even if they did, the good news is that the folks at TinyURL have already blocked the link - preventing the unwary from being caught out. Source: Graham Cluley, Sophos Weblog |
Jun 8, 2010 10:00 PM
#16
| Changelog 07.06.2010: Hackers spam out malware attack Have you received a curt email in the last 24 hours with a mysterious attachment called Changelog_07.06.20010.zip? If so, you could be at risk of falling victim to the latest attack launched by malicious hackers. Poisoned emails have been spammed out worldwide, posing as a legitimate communication.  Typical emails have the following characteristics: Subject: Changelog 07.06.2010 Message body: Good afternoon, as promised, <Name> or Dear customers, as promised, <Name> or Good morning, as promised, <Name> or Good day, as promised, <Name> Attached file: Changelog_07.06.20010.zip where <name> is the first name of the supposed sender of the email. In other words, if the from address says that the message was from "Peter Bathurst" then the email will be signed "as promised, Peter". The intention of all this subterfuge, of course, is to trick you into opening the attachment - perhaps in the hope that you will be able to ascertain what the communication is all about (especially as there is such scant information in the message itself). What's curious, perhaps, is that the subject line (which is presumably designed to match yesterday's date - 7th June 2010) doesn't match the filename, which has a seemingly superfluous zero in the year (Changelog_07.06.20010.zip). Perhaps the hackers behind this malicious campaign had buttery fingers and stumbled as they were creating their attack. However, there are some versions of this attack where the hackers *are* using the "correct" filename of Changelog_07.06.2010.zip. Don't forget the old adage the curiousity killed the cat. Similarly, careless clicking on unsolicited email attachments could lead to the downfall of your data. |
Jun 8, 2010 10:05 PM
#17
Olympus Stylus Tough camera carries malware infection Olympus Japan has issued a warning to customers who have bought its Stylus Tough 6010 digital compact camera that it comes with an unexpected extra - a virus on its internal memory card. The first thing to point out is that the camera itself is not at risk - the autorun worm being carried on its internal memory can not activate on the Stylus Tough camera, but can attempt to infect your Windows PC. In other words, users are at risk of infecting their Windows computers with the autorun worm when they plug the device into their USB drive, a method of transmission effectively identical to the infected Samsung Wave smartphones reported on last week. The next thing to recognise is that not all of the Olympus Stylus Tough 6010 cameras are affected. According to the advisory from Olympus Japan, just over 1700 units are at risk - and customers can check if their camera is carrying the malware by checking their serial number via a widget on Olympus's website (sadly, it's only available in Japanese which won't be too helpful for tourists and businessmen who bought the camera while in holiday in the country).  Olympus says it "humbly apologises" for the incident and that it will make every effort to improve its quality control procedures in future. In the past, other consumer gadgets to have been infected by malware include TomTom satellite navigation devices and Apple Video iPods. Earlier this year, IBM accidentally gave away malware-infected USB sticks at a security conference. With such a long history of incidents like this, more companies need to wake up to the need for better quality control to ensure that they don't ship virus-infected gadgets. At the same time, consumers should learn to always ensure Autorun is disabled, and scan any device for malware, before they use it on their computer. Source: Graham Cluley, Sophos Weblog |
Jun 9, 2010 4:01 PM
#18
| Spam campaign: exploited Excel files There is a recent aggressive spam campaign carrying malicious Excel (.xls) files exploiting a 2009 vulnerability. The Excel file attempts to decrypt, drop and run another executable file, which copies itself to <System>\googletoolbar32.exe and creates a registry entry called “Google Search Engine” to run itself automatically on reboot. Spam is likely to contain the word “treasury” in the sender’s address (which is faked). Examples include: “US Department of Treasury” <noreply@usdot.com> Elizabeth Boucher <elizabeth.boucher_ce@treasury.govt.nz> Chang Avery <c.averysh@treasurytoday.com> Many of the spam messages contain references to OFAC, eg: “Please view the attached report of the declined deposit by OFAC, the file is a Microsoft Excell Spreadsheet.” This vulnerability affects recent versions of Microsoft Excel, and Excel Viewer, so be sure if you have Excel that it is fully updated with patches. Source: Sophos Weblog |
Jun 15, 2010 9:54 PM
#19
| Am I dead? Nigerian 419 scammer wants to know Of course, it's a Nigerian 419 scam and the intention is - ultimately - to trick me into handing over personal information (such as driving license and passport details) and possibly paying them a advance before they (fingers crossed!) transfer millions into my bank account.. but what a wonderful subject line! ARE YOU DEAD? IF NOT GET BACK TO ME IMMEDIATELY  You may not fall for email scams like this - but it's possible that there are more vulnerable and trusting people in your circle who would. Make sure everyone you know is on the lookout for online fraudsters. Source: Graham Cluley, Sophos Weblog |
Jul 7, 2010 7:17 PM
#20
Resignation of Barack Obama virus hoax  Once again a virus hoax is spreading quickly over the internet, forwarded by well-intentioned folk who really should have spent more time researching whether the warning was genuine or not. The warning tells people to look out for emails which have the subject line "Postcard from Bejing" (sic) or "Resignation of Barack Obama" as the attached file can "burn the whole hard C disc (sic) of your computer". Of course, this is nonsense. The warning shares many similarities with other virus hoaxes we have seen in the past including Olympic Torch, Virtual Card for You and Sector Zero. The typical text of the hoax warning reads as follows: Subject: FORWARD THIS WARNING AMONG FRIENDS, FAMILY AND CONTACTS PLEASE FORWARD THIS WARNING AMONG FRIENDS, FAMILY AND CONTACTS! You should be alert during the next few days. Do not open any message with an attachment entitled 'POSTCARD FROM BEJING' or 'RESIGNATION OF BARACK OBAMA ', regardless of who sent it to you. It is a virus that opens A POSTCARD IMAGE, then 'burns' the whole hard C disc of your computer. This virus will be received from someone who has your e-mail address in their contact list. This is the reason why you need to send this e-mail to all your contacts. It is better to receive this message 25 times than to receive the virus and open it. If you receive a mail entitled 'POSTCARD FROM BEJING' or 'RESIGNATION OF BARACK OBAMA' even though sent to you by a trusted friend, under no circumstance, do not open it! Shut down your computer immediately. This is the worst virus announced by CNN last evening. It has been classified by Microsoft as the most destructive virus ever. The virus was discovered by McAfee yesterday, and there is no repair yet for this kind of virus. This virus simply destroys the Zero Sector of the Hard Disc, where the vital information is kept. COPY THIS E-MAIL, AND SEND IT TO YOUR FRIENDS. REMEMBER: IF YOU SEND IT TO THEM, YOU WILL BENEFIT ALL OF US. Hoaxes like this exist because it's so easy to forward an electronic warning to all of your friends and colleagues, and many people who may be suspicious of the warning decide it's better to be safe than sorry. Internet users should think very carefully before they send a message on to all of their contacts, as they may be perpetuating an irritating hoax. You should always check to see if it is believable, and not a known hoax, before even considering sending it onto other computer users. It's worth remembering that hoaxes can cause serious problems, as innocent users over-react to the alert. Sometimes users become convinced that they have become infected by the bogus virus, and when their anti-virus software "fails" to find the infection resort to deleting critical files or formatting their hard drive. Virus hoaxes aren't just a nuisance, they're a menace. By forwarding these hoaxes to your friends and family you could be panicking them into taking the worst possible action. |
Jul 8, 2010 6:17 PM
#21
| Beware 'Your log 05.07.2010' emails Malicious hackers are spamming out emails around the world disguised as a changelog, with the intention of infecting recipient's Windows computers with the attachment.  A typical email reads as follows, although there can be minor variations in the message body: Subject: Your log 05.07.2010 Message body: Dear Customers, as promised your changelog is attached, <name> Attached file: Changelog_05_07_2010.zip The emails, by the way, are always signed off by the first name of the person who is mentioned in the message's from: field. That field is, of course, forged - it's not really that person who sent you the email so don't blame them if you get infected! Clearly the attachment's filename has been chosen to make the email seem more timely, and the hackers are banking on users who receive the message being inquisitive enough to open the file to see what it is regarding. Once again, that would be a bad decision - don't forget that curiosity killed the cat. Source: Graham Cluley, Sophos Weblog |
Jul 8, 2010 6:22 PM
#22
| Contract_05_07_2010.zip - all you'll contract is a malware infection There seems to be another widespread malicious spam attack being sent to email addresses around the world. The emails, which have a malware-infected attachment called Contract_05_07_2010.zip, pretend to be a legal contract - however, opening the contents of the file could infect your Windows computer.  A typical email reads: Subject: Permit for retirement Message body: Good day, We have prepared a contract and added the paragraphs that you wanted to see in it. Our lawyers made alterations on the last page. If you agree with all the provisions we are ready to make the payment on Friday for the first consignment. We are enclosing the file with the prepared contract. If necessary, we can send it by fax. Looking forward to your decision. "<name> Attached file: Contract_05_07_2010.zip Like the other malicious spam attack in post #21, each email is signed-off by the name contained in the email's from: header, albeit with an errant " prefixing it. One can only assume that the superfluous quotation mark was a programming boo-boo by the hackers. Other subject lines used in the attack include: Permit for retirement Contract of settlements Record in debit of account Your new labour contract Loan contract Open an account Rent contract It's interesting to see the cybercriminals use the non-American spelling "Labour" rather than "Labor", which may give some clues as to where they learnt the English language. Mind you, it could just as easily be a red herring as to the emails' origin. Source: Graham Cluley, Sophos Weblog |
Jul 8, 2010 6:51 PM
#23
| Remote Control Facebook App According to AVG, they are now aware of a unique Facebook remote control app that could potentially be malware. They're still in midst of figuring what exactly is it's intention. The initial lure is a link that says that 99% of people can’t watch this video for more than 25 seconds. When you click the link, you are confronted with another screen that offers to show you a video, but, for the video to load, you need to copy and paste some code into the browser address bar. If you are paying attention, you'd notice that you are adding Javascript to your address bar, and you might smell a rat, and stop at this point. If you are not paying attention, you are taken to a page which automatically tells all your friends that you like the app, and it posts that link to your status. It must be effective, because at the time of writing, it had nearly 600k “friends” that liked it. It’s not clear what the payload is at this point, because we’re still figuring it out, but it’s probably one of the sites that wants to charge you $9.95 a month automatically to your mobile phone account. Source: AVG Blogs |
Jul 9, 2010 11:58 PM
#24
| Microsoft to patch Google engineer's zero-day next week Microsoft today said it will deliver four security updates next week to patch five vulnerabilities in Windows and Office, including the bug that a Google researcher took public a month ago. As expected, the slate for next Tuesday is relatively short: Microsoft has been shipping alternating large and small batches of fixes, with the larger updates landing in even-numbered months. In June, for example, the company issued 10 bulletins that patched a record-tying 34 vulnerabilities. May's collection, meanwhile, amounted to just two bulletins that fixed two flaws. "This month is light, and would have been even lighter if Tavis hadn't forced them to move faster than their norm [to patch his vulnerability]," said Wolfgang Kandek, the chief technology officer of Qualys. Kandek was referring to Tavis Ormandy, the Google security engineer who published attack code in early June for a bug in Windows XP's Help and Support Center, a feature that lets users access and download Microsoft help files from the Web, and can be used by support technicians to launch remote support tools on a local PC. The bug, Microsoft said today, also affects Windows Server 2003. Ormandy has been at the center of controversy since he publicly disclosed the vulnerability five days after reporting it, when he said Microsoft wouldn't commit to a patching deadline. While some security researchers criticized Ormandy for taking the bug public, others rose to his defense, blasting both Microsoft and the press -- including Computerworld -- for linking Ormandy to his employer, Google. Last week, a group of anonymous researchers who called themselves the Microsoft-Spurned Researcher Collective (MSRC) -- a play on the acronym used by the Microsoft team bug-investigation team -- retaliated by releasing information about an unpatched vulnerability in Windows Vista and Server 2008. The group published its bug report because of what it said was Microsoft's "hostility toward security researchers," and cited the Ormandy incident as the most recent example. "This shows that Microsoft can move very quickly when it's necessary," said Kandek of Microsoft's patching speed. According to Jerry Bryant, a group manager with the Microsoft Security Response Center, the company was in the preliminary stages of its investigation when Ormandy went public. Ormandy contacted Microsoft on June 5, and two days later, said Bryant, Microsoft told him it could not discuss a patch schedule until the end of that week. "We were in the early phases of investigation when details on this issue were publicly released on June 9," said Bryant in an e-mail Thursday. "By the end of that week our plan was to try and push this into the August release cycle [but] we accelerated our efforts when the risk to customers went up due to active attacks." Hackers quickly put the vulnerability to use, launching attacks five days after Ormandy publicized the flaw. Last week, Microsoft claimed that it had tracked attacks using exploits of the Help Center bug against more than 10,000 computers since June 15. Bryant also credited the fact that Ormandy's bug affected just two versions of Windows for making it possible to push out a patch in five weeks. Microsoft's monthly advance notification sketched out next week's updates: Three of the four updates will be rated "critical," the company's highest threat ranking, while the fourth will be tagged as "important," the next step down. Also on tap is a fix for another already-acknowledged bug, this one in the 64-bit versions of Windows 7 and Windows Server 2008 R2. Microsoft confirmed that flaw in mid-May. Both updates aimed at Windows will be critical, while one update for Office will also be critical, the other as important. The Office updates will plug holes in Access and Outlook, the suite's database and e-mail clients, respectively. Tuesday's updates will be the last for Windows 2000 and Windows XP Service Pack 2 (SP2), both which will be retired from security support that day. Microsoft will release the four updates at approximately 1 p.m. ET on July 13. Source: Computerworld |
Jul 13, 2010 7:13 PM
#25
Is Amazon sending you a Sony Bravia? Beware the malware attack Have you received an email from Amazon about a purchase of a Sony Bravia television? If so, it's possible that you are in the gunsights of hackers behind a malware attack which is being seen around the world which is striking thousands of people who have shown no interest in ordering a new Sony television from the popular online store. Bogus emails, which pretend to come from a manager at Amazon, thank you for shopping at Amazon.com and say that a Sony Bravia TV is winging its way to your address. Subject: Your order has been paid! Tracking NR:26958-480 Attached file: AMAZON_LABEL_07_07-2010.zip Message body: Good morning, Thank you for shopping at Amazon.com! We have successfully received your payment. Your order has been shipped to your billing address. You have ordered " Sony Bravia S3262 " You can find your tracking number in attached to the e-mail document. Print the postal label to get your package. We hope you enjoy your order! Maricela Ruffin, Amazon The emails (which use slight variations in the subject line, the name of the alleged Amazon employee, and the model number of the Sony Bravia television) contain an attached file called AMAZON_LABEL_07_07-2010.zip. If you're befuddled by the email in your inbox out of the blue then the most natural thing in the world might be to open the attachment in an attempt to determine what's going on - especially if you're worried your credit card may have been erroneously charged for some expensive TV hardware. And that's where you would be making a big mistake. The emails are, of course, malicious. This isn't a new trick for cybercriminals to use of course. In the past we've seen other dangerous emails posing as Amazon shipment updates - an order for a Sony VAIO laptop computer, for instance. Source: Graham Cluley, Sophos Weblog |
Jul 13, 2010 7:24 PM
#26
| Malicious 'Payment request from' email attack strikes inboxes Malicious hackers have spammed out the latest incarnation of a campaign designed to compromise your computer - this time disguising their emails as though they were payment requests from eBay. The emails have a blank message body, but have a file called form.html attached.  Message characteristics: Subject: Payment request from From: "eBay" <eBay@reply1.ebay.com> Attachment: form.html Of course it's a sneaky piece of social engineering on the behalf of the hackers. Many people would be tempted to open the attachment to find out what on earth the email is about. Opening the attachment redirects your web browser to a recently compromised webpage on a legitimate site infected with Mal/Iframe-Q (this malware will infect your computer with more various types of malware.) Firstly, your browser is redirected to a spam-related website (for instance, a Canadian pharmacy store). This may make you believe that the attack is merely designed to advertise medications on behalf of the spammers.  Furthermore, however, a malicious iFrame also downloads further malware from other third-party websites. This malware can obviously be changed at anytime, but we have seen versions of the ZBot family of malware be distributed in the attack. As always, the best defence to protect your inbox is to run up-to-date security software (for instance, companies should be scanning their email for combined spam and malware attacks like this) and always be wary of opening unsolicited attachments. And don't forget - the emails don't have to pretend to be from eBay to be malicious. Source: Graham Cluley, Sophos Weblog. |
Jul 13, 2010 7:30 PM
#27
The truth about the Facebook Knob Face worm "Virus spreading like wildfire on Facebook!! It is a Trojan worm called "Knob Face". It will steal your info, invade your system and shut it down! DO NOT open the link "Barack Obama Clinton scandal". If "Smartgirl 15" adds you, don't accept it; it is a virus. If somebody on your list adds her then you will get the virus too!! Copy and paste to your wall please" Let's look at this bit by bit, and see if we can get to the truth. 1. There isn't a virus (or indeed a "Trojan worm" - whatever that is..) called "Knob Face". There is a family of malware called Koobface, but it seems to me that "Knob Face" is an unfortunate spelling mistake. Most variants of the warning that I've seen spreading do refer to "Koob face" which I suppose is a lot more helpful, and significantly less chortle-worthy. 2. Although it is possible for malware authors to hide their attacks disguised as sex videos of the rather unlikely coupling of Hillary Clinton and Barack Obama, the only references to "Barack Obama Clinton Scandal" we're seeing on Facebook right now is in the form of these widespread warnings not malware attacks. 3. As I've mentioned before - the warning about "Smartgirl 15" (sometimes Smartgrrl15") is a hoax which is showing no signs of dying off. Well-meaning Facebook users are perpetuating the bogus warning to look out for the user, believing they are helping their friends. So, in summary, what you have here is a widespread warning about a virus called "Knob Face" (the wrong name), which includes two inaccurate pieces of information about how you can identify the attack. In other words, it's no use at all as a warning. You would be much wiser to keep your anti-virus software up-to-date (to protect against the Koobface worm), take care about what programs you run and links you click on (for instance, be suspicious of links to sexy videos), and read our guide for better privacy and security on Facebook. Please don't share virus warnings with your online friends until you have checked them with a credible source (such as an established computer security company). Malware can be killed off fairly easily, but misinformation like this can live on for months, if not years, because people believe they are "doing the right thing" by sharing the warning with their friends. Source: Graham Cluley, Sophos Weblog |
Jul 15, 2010 6:33 PM
#28
| Mozilla pulls password-sniffing Firefox add-on Mozilla has issued a warning that a Firefox add-on available from the official Mozilla Add-Ons website was secretly sending users' stolen passwords to a remote location. "Mozilla Sniffer" was uploaded to the Firefox add-on site on June 6th, but was only determined at the start of this week to contain code that sent the contents of website login forms to a remote location. In other words, if you installed this add-on (and according to Mozilla about 1800 people did) then everytime you entered your password on a website you were potentially handing over your confidential login details to an unknown party. And this isn't the first time that Firefox add-ons have made the security headlines. For instance, earlier this year Mozilla revealed that the Master Filer add-on was infected by the LdPinch password-stealing Trojan. Back then Mozilla said it would strengthen its vetting procedures, scanning all add-ons with additional anti-virus tools. Clearly that wasn't enough in this latest breach, and there is a proposal to introduce a requirement that all add-ons be code-reviewed before they are published on the site. More details on this proposal are available in a document about the new review model. Mozilla has now block-listed the "Mozilla Sniffer" add-on, meaning that users who are already running the code will be promoted to remove it. If you're one of the potential victims, however, I would go further than just removing the add-on. Make sure you change your passwords too. In a separate security incident, Mozilla has warned that a security vulnerability exists in a version of the popular CoolPreviews add-on (which displays thumbnails of websites when you hover your mouse over web links). Version 3.0.1 and earlier versions of CoolPreviews are said to be affected.  Mozilla says that currently 177,000 users have a vulnerable version of CoolPreviews installed - and has encouraged all users to update to the latest version as soon as possible in order to avoid exposure to attacks. Source: Graham Cluley, Sophos Weblog |
Jul 15, 2010 6:38 PM
#29
| The 'Never gonna drink Coca Cola again' Facebook scam If one of your friends said they were never going to drink Coca Cola again after watching a horrific video, would you be tempted to watch the video? Judging by the number of Facebook users who have posted status updates claiming they are never going to drink Coca Cola again, it seems plenty found it an invitation impossible to resist.  A typical message reads: <name> I am part of the 98.0% of people that are NEVER gonna drink Coca Cola again after this HORRIFIC video --> http://www.[removed] Find out the TRUTH about Coke!!! If you do click on the link you will find yourself on a website saying that "9/10 People said they WOULDNT drink Coca Cola After seeing this video!!!" above a thumnail of a video which says that "Coca Cola can't hide its crimes".  Perhaps surprisingly, this webpage isn't exploiting the now familiar clickjacking technique to falsely claim that the Facebook user "Like"s the page without the user's permission. Instead, they say you can't watch the "horrific video" until you've shared the link on Facebook by hand seven times.   The page claims to poll whether you have shared the link enough (in order to allow the video to be viewed). But when you realise you're not making any progress - despite your valiant attempts to recommend the link to all and sundry - you might hit the link which says: >>>Cant Be Botherd To Wait? --> Click Here To Skip This<<< And this link takes you to a survey which asks you for all sorts of personal information. So, let's recap. You're on Facebook. One of your friends posts that they are part of the 98.0% of people that are never going to drink Coca Cola again after watching a horrific video. You visit the link to see what all the fuss is about, click on "Like" or "Share" umpteen times to distribute the link to your friends, and end up answering all kinds of questions and giving away personal information. Meanwhile, all your friends are also clicking "Like", posting links to their friends, answering questions and giving their personal data away, and never actually seeing what they started out wanting to see. Meanwhile their friends.. and so on.. Source: Graham Cluley. Sophos Weblog |
Jul 19, 2010 6:17 PM
#30
| Windows zero-day attack works on all Windows systems It's been a busy 24 hours looking into this newest flaw in Windows. Lots of research has gone into it and most of the results are not good news for Windows users. It is important to think about this attack as two separate pieces, one that is a new zero-day vulnerability that could easily be adopted by any malware author, the other a unique payload that appears to be designed to go after some very specific infrastructure targets. For corporate users (unless you run a power plant, water system or other SCADA system) the important part is the zero-day flaw. Warning: I am about to go a bit geeky. The flaw is in how shell32.dll tries to load control panel icons from applets. By making a specially crafted shortcut pointing to a malicious file, you can make Windows Explorer blindly execute the malicious file when the location of the shortcut is merely browsed to. In this case the malicious file is a rootkit and a dropper that immediately hide the special shortcut (.lnk) files. Allowing executable code to load in the process of trying to retrieve an icon seems like a major oversight in the design of Windows. This will work even with AutoRun and AutoPlay disabled. I don't know why you would plug in a USB storage device if you weren't going to view it in Explorer... This rootkit is particularly nasty as it infects all Windows versions since XP, and as you see here it bypasses all Windows 7 security mechanisms, including UAC, and doesn't require administrative privilege to run. The user I am logged in as in this video is "Bob," a standard user. I expressed concerns last November about people mistaking UAC for a security feature and this unfortunately seems to still hold true. A few hours ago Microsoft released their security advisory and mitigation advice. However, noticeably absent from the list are Windows 2000 and Windows XP SP2 as they are no longer supported since Tuesday. They are, however, definitely still vulnerable. This exploit affects more than just USB devices. According to Microsoft's advisory, it also affects Windows file shares and WebDav, making a very bad situation worse. Let's hope Microsoft has their best team on this to get us a dependable fix very soon. For now, Microsoft advises that you disable icons for shortcuts. Unfortunately, this is highly impractical for most environments. While it would certainly solve the problem, it would also cause mass confusion among many users and might not be worth the support calls. Microsoft also suggests disabling the WebClient service that is used for WebDav. If you are not a Microsoft SharePoint customer this may be a solution, but many organizations rely on SharePoint so this is limiting as well. The malware originally distributed with this flaw is not a big concern unless you run a nuclear power plant and Homer Simpson is using Windows and clicking whatever he pleases (D'oh!). Expect the exploit, on the other hand, to be widely used in short order. Having had the opportunity to play with it and see the simplicity with which it can be used, I suspect it will be too juicy a target to ignore. Source: Chester Wisniewski, Sophos Weblog |
Jul 19, 2010 6:31 PM
#31
| Win32/Stuxnet Signed Binaries On July 17th, ESET identified a new malicious file related to the Win32/Stuxnet worm. This new driver is a significant discovery because the file was signed with a certificate from a company called "JMicron Technology Corp". This is different from the previous drivers which were signed with the certificate from Realtek Semiconductor Corp. It is interesting to note that both companies whose code signing certificates were used have offices in Hsinchu Science Park, Taiwan. The malicious file, named jmidebs.sys, has functions very similar to those originally noted in the system drivers used by Win32/Stuxnet. This driver is responsible for identifying and injecting code into processes running on an infected machine. The injected code seems to be responsible for stealing information. The compilation date for this latest binary is July 14th 2010, much more recent than the files previously seen, which dated from earlier this year. This new information is important because it provides more information on the people behind Win32/Stuxnet. We rarely see such professional operations. They either stole the certificates from at least two companies or purchased them from someone who stole them. At this point, it isn't clear whether the attackers are changing their certificate because the first one was exposed or if they are using different certificates in different attacks, but this shows that they have significant resources. Source: ESET Threatblog |
Jul 20, 2010 6:12 PM
#32
In-store Fuji photo kiosks spread malware Earlier this month reports began to come in from Australia that some Windows-based Fuji photo kiosks were infected by malware, and spreading worms to unsuspecting shoppers when they inserted their SD cards and memory sticks to print out their digital snaps. Now it appears that FujiFilm is installing anti-virus protection onto its devices. And about time too. But it's not the only solution, of course. Another way to prevent these self-service photo kiosks from passing on an infection like a modern-day Typhoid Mary is to ensure that data can only be read from the customers' SD card or USB stick, not written to it. At least that way the device could become infected - but wouldn't spread the malware further. Clearly not running Windows on the device would also reduce the chances of infection dramatically. For their part, Fuji's arch-rivals Sony and Kodak weren't slow to point out to say that their photo kiosk machines had never been infected by malware. Take security into your own hands. If you use these self-serve kiosks to print your digital photographs you might be wise to use an SD card or USB stick that has a little switch to physically write-protect it before you plug it in. After all, the only thing you want over-exposed are your holiday snaps, not your computer security. Source: Graham Cluley, Sophos Weblog |
Jul 21, 2010 6:51 PM
#33
| OMG!! This Mother Went to Jail' Facebook scam spreads virally Today on Facebook many users are spreading a message which claims to link to a picture that caused a mother to be sent to jail.  However, if you click on the link you are taken to a Facebook page which tricks you into sharing the link with all of your online friends with the promise of seeing the "OMG!!" picture. The page is quite insistent, by the way, that you should share the link with your Facebook pals.  As usual, the people behind this promotion are more interested in you sharing their link around (which will help them earn some survey commission and benefit those behind the surveys as they grab your personal information) than actually showing you anything of interest.Far too many people are prepared to endorse and share links on Facebook without properly thinking about what they are doing. In this case they're doing it before they have any clue about what lies behind the page. There are also messages spreading a similar scam virally via Facebook claiming that McDonald's might shut down:  Clicking on the link to see "why McDonald's might soon shut down" takes you to another Facebook page which promises to make your "jaw drop to the floor".  Source: Graham Cluley, Sophos Weblog |
Jul 21, 2010 6:54 PM
#34
| Dell warns of malware on motherboards Dell has published a warning on its support forum that some of its server motherboards are infected with Windows malware. The admission, posted in response to a customer who wished to confirm that a telephone call he had received from a Dell representative was genuine, confirmed that "a small number of PowerEdge server motherboards" may contain spyware in its embedded server management firmware.  Dell says that it has created a list of affected customers, and that they are formally notifying them of the security problem via letter. Unfortunately, no specifics are offered as to which malware has infected the motherboards, or what it does. Even though it is believed that the malware only affects Windows-based operating systems, this is still embarrassing for Dell - and questions will be asked as to whether stringent enough quality control measures were in place to prevent unauthorised code from shipping with their hardware. Source: Graham Cluley, Sophos Weblog |
Jul 21, 2010 6:58 PM
#35
| Malicious shortcuts: now documents and webpages are risky too (This post is related to Post #30) There's more bad news for those troubled by the Microsoft zero-day vulnerability that allows a Windows shortcut link, known as an .LNK file, to run malicious code whenever Windows displays their icon. The exploit, is well known to be capable of spreading via USB sticks, network and remote WebDav shares. But, the latest version of Microsoft's security advisory on the subject also warns that a malicious shortcut file can be embedded on a website (meaning that users who visit the page via their web browser could be infected) or hidden inside documents.  It has also become apparent that .PIF files can also be exploited by the vulnerability, as well as .LNK files. And don't forget - the code for how to exploit this vulnerability has been published in the wild, and Microsoft hasn't yet issued a proper patch for the exploit (their temporary mitigation advice has some usability issues that may actually cause more serious problems inside your organisation than the real malware). Source: Graham Cluley, Sophos Weblog |
Jul 22, 2010 6:11 PM
#36
Justin Bieber's cell phone number? Nope, it's a Facebook scam Do you remember when hardly a week went by without cybercriminals infecting computers with the promise of glimpses of glamorous pin-ups like Halle Berry, Anna Kournikova, Julia Roberts, Jennifer Lopez or Britney Spears? Those days aren't entirely behind us (lets not forget the danger of hunting for sex tapes of Gossip Girl actress Leighton Meester, naked photos of Paramore's lead singer Hayley Williams, and peephole videos of TV sports presenter Erin Andrews) but the one thing they invariably relied upon was a human weakness, or perhaps I should say male weakness. Invariably the "sexy" attacks and scams used nubile young actresses, either caught in compromising positions or posing seductively to boost their careers. And it would - for understandable reasons - mostly be men who would find it hard to resist opening the attachment or clicking on the link. But just as grown men can find that they're suffering from a case of "twitchy mouse finger" (a medical condition which means you have to click on a link even though every sensible neuron in your brain is telling you that it might be risky) so young women find themselves in a state of permanent squee over teen pop sensation Justin Bieber. And, aside from Justin Bieber, what else are young girls addicted to? Facebook. So it's no surprise at all to see the scammers exploiting Facebook with claims that they can give you Justin Bieber's cell phone number if you just share their link with all of your friends.  If you're a fan of the pint-sized prince of pop and find yourself clicking on the "Like" button as the page suggests you'll be taken to a dialog which shares the link to your online friends using the phrase OMG!! Justin Biebers Ex GIRLFRIEND just RELEASED his new CELL PHONE NUMBER!!  Remember, at this point no-one has given you Bieber's cell phone number (real or otherwise), but in your desperation to contact the miniature music munchkin you've still shared the link with all of your Facebook friends (who, chances are, will also be obssessed with Justin Bieber). And I'm afraid that you never will get Justin Bieber's real phone number. The page has been created to redirect your browser to surveys that ask you umpteen questions (gathering your personal information for the companies behind the survey, and earning the scammers some affiliate cash). In some cases the scammers ask you for your cell phone number, and then sign you up for a premium rate service. If you did make the mistake of passing the link onto your friends, you should clean-up your newsfeed and profile to remove references to the link.  The scam works in a very similar way to the "OMG!! Guys, you have to see this: This mother went to jail for taking this pic of her son!" scam in post #33. Source: Graham Cluley, Sophos Weblog |
Jul 24, 2010 1:42 AM
#37
| Want to see who has viewed your Facebook profile? Take care.. A number of people who have been attracted to webpages and Facebook applications that claim to be able to give you a secret insight into who is spying on your profile. Well, if you're one of those people who are curious about who might be watching you online, take care. Right now we're seeing a significant number of Facebook users posting messages such as: OMG OMG OMG... I can't believe this actually works! Now you really can see who views your profile!!! WOAH and See who views your Facebook profile in real-time!!!  However, like the "Justin Bieber cell phone number" scam and the "This mother went to jail for taking this pic of her son!" scam, the links pointed to in your friends' status updates are not to be trusted. If you make the mistake of clicking on the link to one of these pages offering to tell you who is viewing your Facebook profile, you will find that the people behind the "services" want you to do a few things first.  For instance, they'll ask you to "Like" their pages (which means you are spreading the link to friends in your social network), and they will ask you to advertise their site by posting an "OMG" message (with a link) to at least five different places on Facebook. After all that hard work you would hope that they would give you access to the powerful Profile Spy app wouldn't you? But I'm afraid your luck is out. They'll next ask you to hand over your personal information by taking numerous surveys - before ultimately trying to trick you into handing over your cellphone number which they'll sign up to an expensive premium rate service. [mg]http://www.sophos.com/blogs/gc/images/blogs/gc/2010/07/see-who-viewed-profile-2.jpg[/img] Remember, this scam doesn't work as the result of clickjacking, or a vulnerability on Facebook. The scammers are achieving their ends because of human gullibility - pure and simple. If people considered what they were doing and thought twice about the possible consequences then we would see nothing like as many of these attacks occurring, and our news feeds on Facebook would see less spam. Interestingly, the pages that this particular scam points you to aren't on Facebook, but still display a fake Facebook header at the top. You will notice if you visit them that although the top menu options are there, they cannot be clicked on - which clearly makes the pages look even more suspect. Ultimately, you have to have your wits about you to avoid scams like this. Source: Graham Cluley, Sophos Weblog |
Jul 27, 2010 6:57 PM
#38
| Citi iPhone banking app contains security flaw iPhone-owning customers of Citigroup have been urged to update their mobile banking app immediately because of a security flaw that secretly stored account numbers, bill payments and security access codes in a hidden file. The Citi Mobile app allows customers to check their account balances, transfer funds and pay bills from their iPhone, and is one of the most popular finance applications in the Apple App Store with approximately 120,000 users since it was launched in March 2009. Citigroup told the Wall Street Journal that it had "no reason to believe that our customers' personal information has been accessed or used inappropriately by anyone."  However, there will undoubtedly be concerns that if users lost their iPhone the information could be accessed by an identity thief. Furthermore, it is believed that the sensitive data could also have been backed-up to customers' Windows and Mac computers when they are synchronised with the iPhone. Certainly, there are many more chances for the typical malicious hacker to access information stored on a PC than on the controlled environment of an Apple iPhone. The good news is that the iPhone has a pretty slick system for notifying users that there is an update available for their installed apps, meaning it should only take a couple of clicks for users to upgrade their version of the Citi Mobile app to a more secure version. Source: Graham Cluley, Sophos Weblog |
Jul 27, 2010 7:02 PM
#39
| Windows Shortcut Exploit: Interim Protection Measures Sophos has released a software that could protect your Microsoft OS from the current Shorcut Vulnerability. This only works on Windows XP, Vista and Windows 7. To download, please click here. |
Jul 29, 2010 5:51 PM
#40
Android malware steals info from one million phone owners A developer of Android apps has been accused of using their apps to steal information from more than one million smartphone users. John Hering and Kevin MaHaffey, of mobile security firm Lookout, told the Black Hat security conference in Las Vegas that they discovered that a wallpaper app developed by Jackeey Wallpaper (who have created over 70 different applications for the Google Android mobile operating system) secretly transmitted affected phones' numbers, subscriber identifiers, and voicemail numbers to a server in Shenzen, China. Over a million people are believed to have downloaded the app from the Android Market (Google's equivalent to the Apple iPhone AppStore). This isn't the first time that the Android smartphone operating system has been targeted by malware, of course. One of the challenges that owners of smartphones running the Android operating system face is that it is not as closely monitored as Apple's equivalent, and adopts a more relaxed philosophy as to what apps can be published. Although there's much criticism that Apple has received for the way it controls the iPhone environment, it's clear that the only malware attacks we've seen to date on that platform (such as Duh and the infamous rickrolling Ikee worms) have affected users who have chosen to jailbreak their iPhones and escape the relative safety of the AppStore. Yes, malware has previously emerged for jailbroken iPhones, but the malicious applications have not made it onto users' devices via Apple's highly guarded AppStore. It remains to be seen how many users will treat security as a factor when choosing between the rival mobile operating systems. |
Aug 1, 2010 6:26 PM
#41
| Shocking real crimes on Google Streets? No, it's another viral Facebook scam Once again a viral scam is spreading rapidly across Facebook, posting messages on users' profiles in an attempt to trick the unwary into installing a rogue application. Many Facebook accounts are currently posting messages saying:  OMG! Shocking Real Crimes caught live on Google Streets. This is SO Unbelievable and you have got to see it! hxxp:/tiny.cc/urztb At first glance you may believe that your friend genuinely thinks that you will be interested in viewing what's at the end of that link, but the fact of the matter is that it wasn't your Facebook friend who posted that message - but a rogue Facebook application called Earth Finder. If you do fall for the social engineering trick and click on the link you are taken to a Facebook page which says:  Google Street View Big Brother is constantly watching us and does so all the time. These Crooks thought that they were above the LAW and could get away with anything. Unfortunately for them, Google Streets caught them red handed and on FILM! See the world's most EMBARRASSING and SHOCKING CRIME photos that were caught live on Google Streets. [Click Here to See The CRIMES] By now you're hooked, and quite possibly desperate to find out what embarrassing and shocking photographs of criminals you might be about to be shown (remember, it was your friend's Facebook account which has recommended this content after all). But going any further takes you to a page which tells you you need to give permission to a Facebook application called "Earth Finder" first. And that's where things really begin to go wrong. Because now you've given the green light for "Earth Finder" to post messages from your Facebook profile, advertising it to all of your friends.  And once again (like the recent "Teacher Nearly Killed This Boy" application) you will be making money for the scammers by being redirected to a series of surveys and online questionnaires. If you've fallen for a scam like this, spreading virally across Facebook, make sure you clean up your Facebook account - remove the references to it from your status updates and news feeds, and ensure that you have zapped it from your list of applications. Source: Graham Cluley, Sophos Weblog |
Aug 2, 2010 8:39 PM
#42
| Rude Toy Story 3 hidden message? It's another Facebook scam The recent release of the Toy Story 3 movie is making waves not just because of its ability to make middle-aged men weep, but also because of a message that is being shared far and wide across Facebook:  SHOCKING: RUDE HIDDEN MESSAGE IN Toy Story 3! See the SHOCKING picture! Hardly ANYONE notices this when watching Toy Story 3 As the message appears to have been posted by one of your Facebook friends, you may well be curious to see what it is that he or she is pointing to, and click on the link. Clicking on the link, however, takes you to a page which insists that you "Like" the page before showing you the "sick hidden message" from the blockbuster Pixar movie.  Of course, if you "Like" the page you are - in effect - advertising it to your fellow Facebook friends. But the page doesn't stop there, it also insists that you endorse the page further by sharing the link in a post to your Facebook wall.  It's frankly alarming how many people will go along with this even though they still haven't seen any "shocking picture" and have no idea what it may be that they are promoting (or indeed on whose behalf they might be promoting the page). The motive for this scam, which already appears to have recruited hundreds of thousands of fans, is to direct unsuspecting users to an online survey (which you are told is compulsory if you wish to view the Toy Story 3 content). The scammers make money for the traffic they bring to the survey, and the survey-makers will benefit from collecting your data. You, however, should refuse to play ball. Don't agree to "like" or "share" pages which you don't have a good reason to approve. If you have fallen for a scam like this, ensure that you delete references to it in your news feed and remove the application from the list of pages that you "like".   After all, what good reason is there to share this scam with your friends? Source: Graham Cluley, Sophos Weblog |
Aug 4, 2010 6:21 PM
#43
| Justin Bieber's naughty webcam is another Facebook viral scam The Facebook survey scammers are up to their dirty tricks again, this time trying to trick you into believing that pint-sized pop phenomenon Justin Bieber has been naughty on his webcam. For at least the last 24 hours messages have been appearing on the social networking service, seemingly posted by innocent users, saying:  Did you saw how Justin Bieber become naughty on his webcam? Justin Bieber become naughty on his webcam - shocking video! Justin Bieber like you never saw before. Clicking on the link takes you to a page which poses as a video of Justin Bieber engaged in a webcam video chat with a female admirer. According to the page, Justin Bieber asked random girls on the internet to tease him on his webcam (something, you imagine, that his frenzied female followers might be all too willing to do).  OMG! Justin Bieber Webcam scandal revealed! Justin asked random girls to tease him on webcam what they will do ? what he will do ? you will be in shock when you will see the full video ! However, if you were desperate to watch the alleged video you'll have to jump through some hoops first. As is usual with these type of scams, the pages want you to "Like" and "Share" their contents on Facebook before they will let you see the "shocking video". If you're in any doubt as to whether this is a wise course of action or not, the page displays some "reviews" from other fans confirming how "shocking" and "naughty" the video is.  So, the scammers are trying to get you to share the link as much as possible - with the promise of showing you a shocking video of Justin Bieber flirting on a webcam at the end. Their hope is that you will share the link far and wide, increasing the number of people who might want to go through with the process and - ultimately - take an online survey. Surveys like this not only scoop up your personal information, but also earn commission for the people who are spreading these links around. In the worst cases they even ask for your cell phone number and sign you up for expensive premium rate services. It's time that Facebook users got wise to this trick, and refused to play ball. If there really is a sensational shocking video of Justin Bieber you can be pretty sure that it will be appearing on a sleazy TV news station pretty soon, rather than being hidden behind Facebook pages that make you take surveys and pass on their links. This isn't the first time that Justin Bieber has been used as bait by internet scammers, and it won't be the last. If you fell for the scam, remove references to it from your profile and newsfeed. In particular, make sure that you have also removed it from the list of "Movies" you like, where it has sneakily placed itself for others to stumble across:  Interestingly, we're also seeing some attempts to spread this scam via Facebook, apparently deliberately targeting those with an interest in Justin Bieber:  Source: Graham Cluley, Sophos Weblog |
Aug 4, 2010 6:23 PM
#44
| Shocking video of a girl attacked by a shark? OMG - it's a colourful clickjack attack Hot on the heels of other recent scams spreading virally across Facebook, we're now seeing another - this time posing as a link to an alleged shocking video of a girl being attacked by a shark. Thousands of messages have been posted by Facebook users reading: OMG The Most Shocking Video Caught On Camera Girl Being Attacked By A Shark  If you click on the link you are taken to a Facebook page which fools you into believing you are about to watch a video. All you need to do (they say) is click on the red button and the blue button.  If you agree to click on the coloured buttons, then you are actually being clickjacked - secretly liking and sharing the link with all of your Facebook friends. You're in good company at least - thousands of other Facebook users have done the same..  And now you're a fan of that page they're free to send your updates and messages, and potentially spam you or send you malicious links. What's worse - you've endorsed the page and shared it with your online mates. Source: Graham Cluley, Sophos Weblog |
Aug 5, 2010 6:48 PM
#45
| Attack of the Twitter babes - Tweets that ain't so sweet The latest spam campaign we've seen on Twitter involves a bevy of beauties. Here are just a small number of the profiles I have seen, all with images of young attractive women (and/or in a state of undress):  All of them have recently created Twitter accounts (the last week or so), and all of them are tweeting identical messages pointing users to a service called Tweet Attacks - which encourages you to buy a program that, it says, will help you make money via Twitter. I don't know what the Tweet Attacks program does, but if it's in any way involved in this spam campaign I would stay far away. If you want more followers on Twitter there's a very simple, tried-and-trusted, method: tweet something that other people might find interesting. Source: Graham Cluley, Sophos Weblog |
Aug 7, 2010 12:03 AM
#46
| Girl who killed herself virus hoax spreads on Facebook Many Facebook users are spreading inaccurate messages on the social network, warning each other to beware a "virus" that claims a girl killed herself over a post her father made on her Facebook wall.  The text of the warning reads as follows: WARNING:THERE IS A VIRUS GOING AROUND AGAIN, IF YOU SEE A GIRL WHO KILLED HERSELF OVER SOMETHING HER FATHER WROTE ON HER WALL DO NOT OPEN IT, IT IS A VIRUS AND IT WILL NOT ALLOW YOU TO DELETE IT, PLEASE PASS THIS ON BEFORE SOMEONE OPENS IT. (IT IS A SELF REPLICATING TROJAN) However, the alerts are not based on facts, and members of the public are unwittingly perpetuating a hoax in the belief that they are helping their online friends and family avoid a nasty virus infection. Ironically, the warning about the hoax is spreading faster and wider, and is probably more of a nuisance, than any genuine infection. For those who care about such things, viruses and Trojan horses are different types of malware - it's not possible to have a virus which is a Trojan horse. And by their very nature, Trojan horses cannot be self-replicating. Furthermore, there's no such thing as malware that you can't remove so the claim that it "will not allow you to delete it" is nonsense too. Okay, now that's clear let's look a little more deeply into this story. What is the background to this virus hoax? It turns out that things are rather complicated. According to internet rumours, a girl called Emma killed herself on Christmas Eve 2008 after being bullied on Facebook. However, images which show the alleged conversation between the bully and victim show "Like" buttons even though it was not possible to say that you "liked" an online conversation on Facebook back in 2008.  Rumours like this get a lot of people's attention - and it has been exploited by the bad guys in what is becoming a genuine problem on Facebook. There are a number of scam Facebook pages which claim to be about the alleged girl who killed herself because of a post made on the site (although some claim it was by her mother, not her father).  Visiting the pages takes you to the familiar scam where they trick you into "liking" and "sharing" the link.  There are also links being shared online which show the picture of a young woman, alleged to have been the person who killed themselves after their father wrote on their Facebook wall.  However, the picture of the woman used on this webpage is actually that of former Greenwich University student Emma Jones. 24-year-old Miss Jones died in Abu Dhabi in November 2009 after drinking poisonous cleaning fluid, and there were claims that she was distressed and commited suicide after her ex-boyfriend had posted naked photos of her onto Facebook. (Before you click on that link, let me advise you that there aren't any naked photos there.) So, despite what this page promises - it's nothing to do with her father writing a message on her Facebook wall. I think it's pretty sick that cybercriminals are using the image of a dead woman in their attempts to spread their scam. However, the worrying thing is that the Facebook page promoting this (and other) scam pages has over 583,000 fans - making it easy for them to advertise a new link and kick start a new campaign at any time.  It seems many people are all too willing to unwittingly help spread such links.  Undoubtedly some of these scams and rogue Facebook pages will have helped fuel the hoax that a virus is doing the rounds. Source: Graham Cluley, Sophos Weblog |
Aug 7, 2010 12:16 AM
#47
| Infected computers on the rise in Mideast, says Trend Micro DUBAI — Internet security company Trend Micro said that the number of computers infected with viruses in the Middle East has dramatically increased due to the lack of adequate security precautions. As of April 2010, there were more than 740,097 infected machines across the GCC — a 116 per cent increase in less than a year. This was observed through Trend Micro’s Smart Protection Network technology, which can see how many computers are active on the Internet and which among these are infected. From 2004 to 2009, the region saw a massive 8,140 per cent rise in the number of infected machines. The rate of infection in the UAE grew by 4,553 per cent, while Saudi Arabia witnessed a staggering 45,072 per cent leap. Other GCC states recorded increases in infected machines — Kuwait, 1,545 per cent; Qatar, 4,468 per cent; Bahrain, 6,047 per cent; and Oman, 8,921 per cent. Ian Cochrane, Trend Micro’s Marketing Manager for the Middle East and Africa region, said that this growth would continue — giving cyber criminals more chances to take advantage — unless it is recognised that the region is vulnerable and steps are taken to protect computers. “The numbers of compromised machines are a key indicator of how well cyber criminals are doing in stealing from this region. The visible infections have more than doubled in less than one year. The bad guys are winning because in this region we are not taking security seriously,” he said. On the other hand, Dave Rand, Trend Micro’s Chief Technology Officer, said that users’ dependence on the Web raises vulnerability and makes them unaware of threats. “Protecting ourselves in the Internet does not have to be complex. We just need professional security software that can block threats and [perform] regular scanning, [as well as] exercising personal caution,” he said. Source: Khaleej Times |
Aug 9, 2010 6:00 PM
#48
| The world's worst McDonald's customer? Beware rogue Facebook app spreading rapidly Thousands of Facebook users are spreading a message to their online friends, urging them to see a "shocking video" that claims to be of the world's worst McDonald's customer.  The messages read: OMG the worlds worst mcdonalds customer (shocking video must see) followed by a bit.ly link. Clicking on the link takes you to a Facebook application called "Worst McD's Customer", which asks permission to post to your wall, access your data at any time, access your contact information and your list of friends, amongst other things.  If you're sensible you'll pull out at this point, and not grant the application permission to access your data. But sadly plenty of people are keen to see the "shocking video" and will hand over control to the rogue Facebook app - which promptly posts the link as a status update to your Facebook wall - thus perpetuating the cycle. If you were foolhardy enough to fall for this trick, remove the references to the link from your newsfeed, clear your status message, and ensure that the application's right to access your account is revoked.  Source: Graham Cluley, Sophos Weblog |
Aug 9, 2010 6:04 PM
#49
| Skype and Contact Request spam All of us are familiar with email-based spam, and more and more people are becoming used to receiving spam via social networks too, but it's also possible to receive spam via other routes too. For instance, you can receive spam messages that are sent to you via Skype. These can either be received in the form of an instant messaging chat session, or - as in the example below - as a bogus Contact Request from someone.  Skype spam is far from a new phenomenon - but as more and more people use the service, more folks are becoming exposed to spam sent via the platform. In the above example, a spammer sends a message pretending to want to make contact with you - but in fact has used the opportunity to advertise their adult "dating" website.  I find it hard to believe that Skype Contact Request spam is as effective as other mechanisms of spamming. Most Skype users would likely ignore the message, and wouldn't be likely to cut-and-paste the link into their browser - but maybe the more curious (or should I say "randy"?) would. However, it's still a nuisance and it's no surprise that Skype users would want to see less of this stuff.There's nothing to stop the spammer creating another Skype account and starting his or her campaign again. Skype says it looks for patterns in spammers' behaviour - but it'll be better if they went one step further and put tighter controls in place regarding the number of Contact Requests that a user can send in a period of time. That would cut many spammers down to size, as would limiting users' ability to write a custom message when they send a Contact Request to another user.  One thing is for sure, even if measures are put in place to reduce Skype contact spam it won't be the end of the spam problem on the network. We're likely to see more and more cases where innocent Skype users' accounts are compromised by hackers and used as a "launching pad" for spam campaigns - whether they be to advertise spammy goods or to spread malicious links. Source: Graham Cluley, Sophos Weblog |
Aug 13, 2010 1:48 AM
#50
Beauty and the Geek malware attack spammed out Hackers are spamming out malware-infected emails, tricking recipients into believing that they are being invited to enter auditions for the reality TV show "Beauty and the Geek". The show, which pairs together beautiful (but perhaps slightly dim) women with intelligent (but possibly rather dorky and socially inept) males, is a worldwide hit - matching the likes of Playboy models and cocktail waitresses with astro-physicists and IT security bloggers. Of course, some fame and a cash prize is probably enough to attract many to consider appearing on the TV programme. But an email being widely spammed out, claims to be looking for new recruits for the US show.  Part of the email, which has the subject line "Beauty and the Geek 2", reads: So... I'm looking for geeks all over USA. They need to be highly intelligent and shy/nervous around girls etc All the contestants genuinely had an amazing time last year and are actively recommending it to their mates this year. They get the chance to teach hot girls a thing or two, and get the chance to win $100,000! So far - I haven’t spoken to a single geek who’s been offended that I’ve called them one. But if you’d rather - please do pass on their details to me and I’ll get in touch with them anonymously. I’ve attached flyers in case you want to forward on, or put up in your office... However, the attached file (flyers.zip) really contains not promotional material for the TV show - but a file called flyers.exe. That executable file is malware, of course, exposing the recipient's computer to attack. The malicious software is a variant of the highly popular trojan Zbot used currently. Always treat unsolicited emails with suspicion - the smart thing to do is to delete this email without opening the attachment, and ensure that your anti-virus software is updated. Source: Graham Cluley, Sophos Weblog |
More topics from this board
Sticky: » Computer IssuesSoujimiSatori - May 11, 2010 |
1 |
by SoujimiSatori
»»
Aug 7, 2010 7:49 PM |
|
Sticky: » IT NewsSoujimiSatori - May 13, 2010 |
4 |
by SoujimiSatori
»»
Jul 8, 2010 7:04 PM |
|
Sticky: » Miscellaneous IT QuestionsSoujimiSatori - May 13, 2010 |
0 |
by SoujimiSatori
»»
May 13, 2010 11:22 PM |
|
» DiscussionsSoujimiSatori - May 11, 2010 |
0 |
by SoujimiSatori
»»
May 11, 2010 8:05 PM |
|
Sticky: » Server IssuesSoujimiSatori - May 11, 2010 |
0 |
by SoujimiSatori
»»
May 11, 2010 7:57 PM |
